How to Create a Self Signed Certificate in IIS 7
SSL is an essential part of securing your IIS 7.0 site and creating a self-signed certificate in IIS 7 is much easier to do than in previous versions of IIS. SSL certificates enable the encryption of all traffic sent to and from your IIS web site, preventing others from viewing sensitive information. It uses public key cryptography to establish a secure connection. This means that anything encrypted with a public key (the SSL certificate) can only be decrypted with the private key and vice versa.When to Use an IIS Self Signed Certificate
Never use a self signed certificate on an e-commerce site or any site that transfers valuable personal information like credit cards, social security numbers, etc.An SSL certificate has multiple purposes: distributing the public key and, when signed by a trusted third-party, verifying the identity of the server so clients know they aren’t sending their information (encrypted or not) to the wrong person. A self signed certificate is a certificate that is signed by itself rather than a trusted third party. This means you can't verify that you are connecting to the right server because any attacker can create a self signed certificate and launch a man-in-the-middle attack. Because of this, you should almost never use a self signed certificate on a public IIS server that requires anonymous visitors to connect to your site. However, self signed certificates can be appropriate in certain situations:
- Self signed certificates can be used on an intranet. When clients only have to go through a local intranet to get to the server, there is virtually no chance of a man-in-the-middle attack.
- Self signed certificates can be used on an IIS development server. There is no need to spend extra cash buying a trusted certificate when you are just developing or testing an application.
- Self signed certificates can be used on personal sites with few visitors. If you have a small personal site that transfers non-critical information, there is very little incentive for someone to attack the connection.
Generate Your IIS Self Signed Certificate
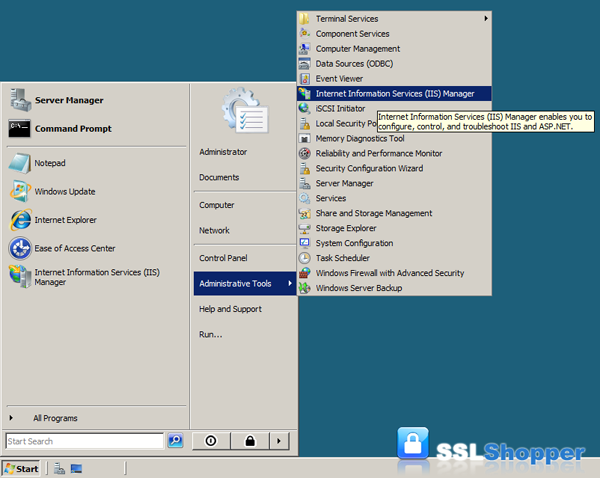
Now you know when to use an IIS self signed certificate and when not to. Now let’s create one: (Click here to hide or show the images)- Click on the Start menu, go to Administrative Tools, and click on Internet Information Services (IIS) Manager.
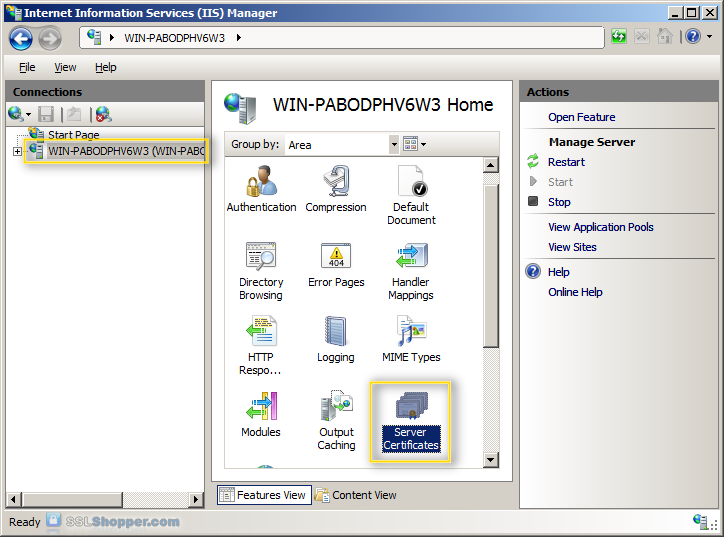
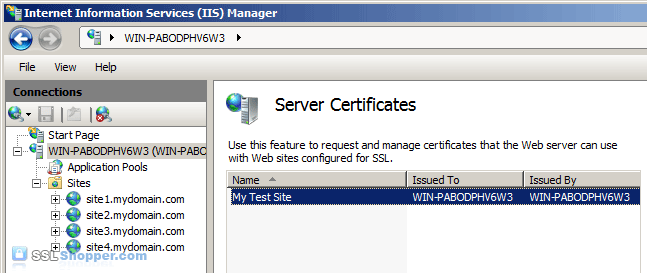
- Click on the name of the server in the Connections column on the left. Double-click on Server Certificates.
- In the Actions column on the right, click on Create Self-Signed Certificate...
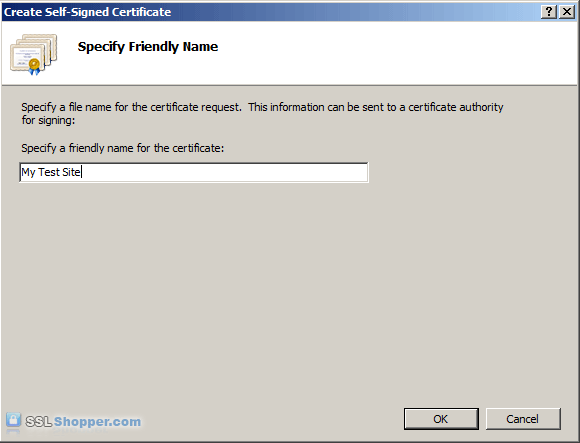
- Enter any friendly name and then click OK.
- You will now have an IIS Self Signed Certificate valid for 1 year listed under Server Certificates. The certificate common name (Issued To) is the server name. Now we just need to bind the Self signed certificate to the IIS site.
Bind the Self Signed Certificate
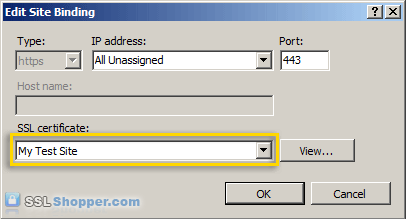
- In the Connections column on the left, expand the sites folder and click on the website that you want to bind the certificate to. Click on Bindings... in the right column.
- Click on the Add... button.
- Change the Type to https and then select the SSL certificate that you just installed. Click OK.
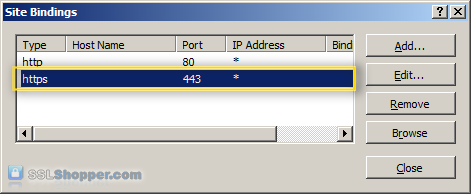
- You will now see the binding for port 443 listed. Click Close.
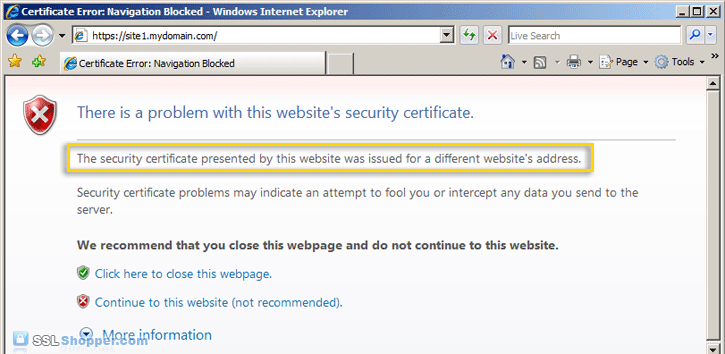
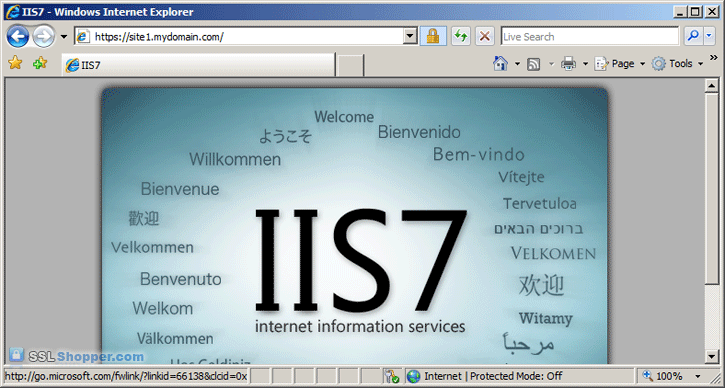
- Now let's test the IIS self signed certificate by going to the
site with https in our browser (e.g. https://site1.mydomain.com). When
you do, you should see the following warning stating that "The security
certificate presented by this website was issued for a different
website's address" (a name mismatch error).
This is displayed because IIS always uses the server's name (in
this case WIN-PABODPHV6W3) as the common name when it creates a self
signed certificate. This typically doesn't match the hostname that you
use to access the site in your browser (site1.mydomain.com). For many
situations where IIS self signed certificates are used, this isn't a
problem. Just click "Continue to this web site" each time. However, if
you want to completely get rid of the error messages, you'll need to
follow the next two steps below.
Generate a Self Signed Certificate with the Correct Common Name
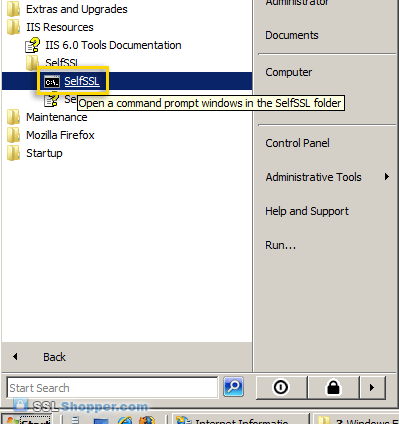
This step is only required if you want to get rid of the warning message displayed because the common name on the self signed certificate doesn't match the website's hostname. In order to resolve this problem, we'll need to create the self signed certificate using the same method that is used to create a self signed certificate in IIS 6.0 (with SelfSSL instead of through IIS).- Download the Internet Information Services (IIS) 6.0 Resource Kit Tools and install SelfSSL 1.0 (if you do a Custom install you can uncheck everything except for SelfSSL). Once it is installed, click on the Start menu, go to IIS Resources, then SelfSSL, and run SelfSSL.
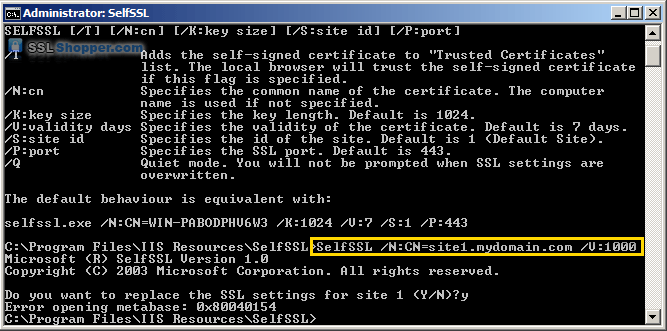
- Paste in the following command and replace site1.mydomain.com
with the hostname of your IIS site. If you receive the erorr "Error
opening metabase: 0x80040154", just ignore it. We will be manually
binding the certificate to the website.
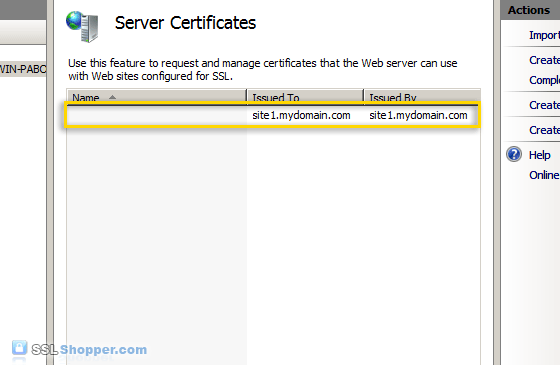
SelfSSL /N:CN=site1.mydomain.com /V:1000 - After the command is finished, you will have an IIS self signed certificate with the correct common name listed in the Server Certificates section of IIS. Now follow the instructions above to bind the certificate to your IIS website.
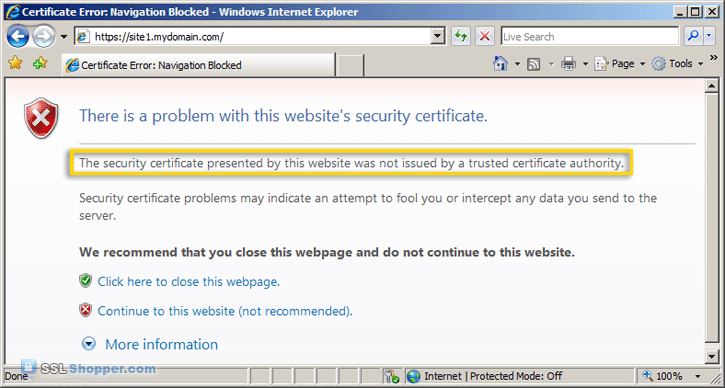
- After you have bound the new certificate to your IIS site, visit it with https in your web browser and you will encounter another error: "The security certificate presented by this website was not issued by a trusted certificate authority." (the SSL Certificate Not Trusted error) Don't worry; this is the last error we will need to fix. This is a normal error for self signed certificates because the certificate is signed by itself instead of a trusted SSL provider. All visitors to the site will see that error unless they import the self-signed certificate into their Trusted Root Certification Authorities store (or the appropriate SSL certificate store for the browser they are using). You can easily add the IIS self signed certificate to the store on the server by following the the instructions below. If you need to import the certificate on another Windows machine, just follow the instructions on how to Move or copy an SSL certificate from a Windows server.
Add the Self Signed Certificate to Trusted Root Certificate Authorities
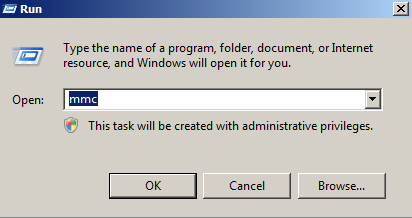
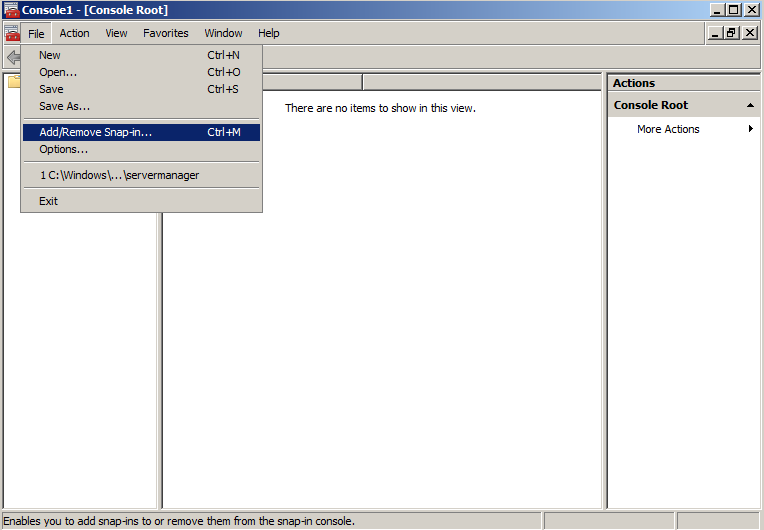
- Click on the Start menu and click Run.
- Type in mmc and click OK.
- Click on the File menu and click Add/Remove Snap-in...
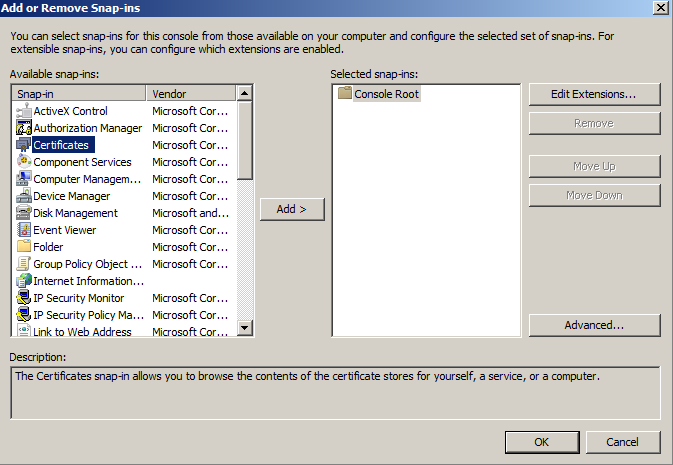
- Double-click on Certificates.
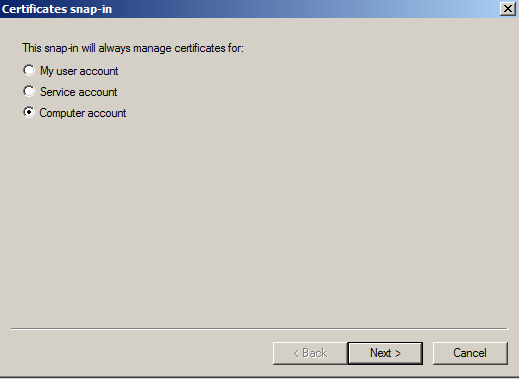
- Click on Computer Account and click Next.
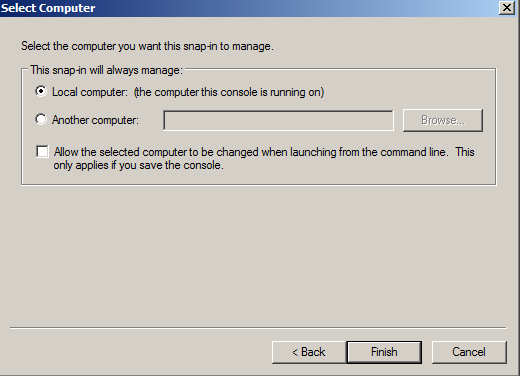
- Leave Local Computer selected and click Finish.
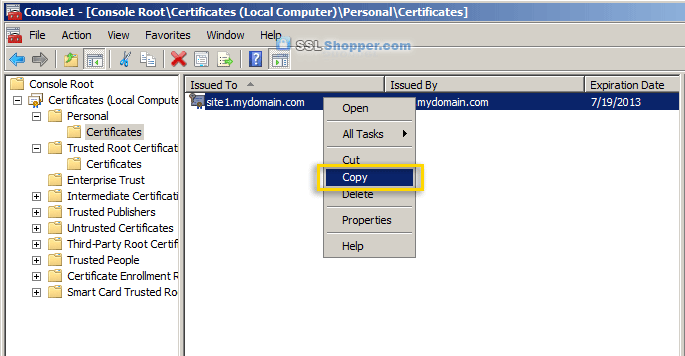
- Expand the Certificates item on the left and expand the Personal folder. Click on the Certificates folder and right-click on the self signed certificate that you just created and select Copy.
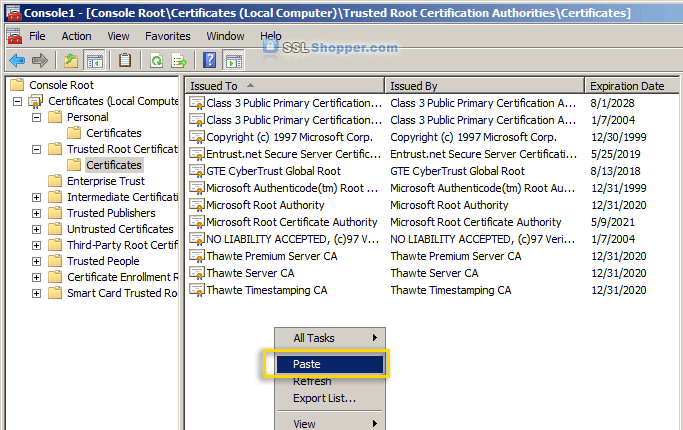
- Expand the Trusted Root Certification Authorities folder and click the Certificates folder underneath it. Right-click in the white area below the certificates and click Paste.
- Now you can visit your site with https in your web browser and you shouldn't receive any errors because Windows will now automatically trust your IIS self signed certificate.
- Installing an SSL Certificate in Windows Server 2008 (IIS 7.0)
- Tip/Trick: Enabling SSL on IIS 7.0 Using Self-Signed Certificates
- IIS Self Signed Certificates on IIS 7 – the Easy Way and the Most Effective Way
Reply #17 on : Fri May 04, 2012, 01:33:18
Bryan Bowers
Posts: 15
Posts: 15
Reply #16 on : Mon April 30, 2012, 15:35:16
Rix
Posts: 15
Posts: 15
Reply #14 on : Fri April 27, 2012, 00:49:29
Ted
Posts: 15
Posts: 15
Reply #13 on : Fri January 20, 2012, 16:07:51
Mithun Kanji
Posts: 15
Posts: 15
Reply #12 on : Mon January 16, 2012, 04:32:11
Jeff
Posts: 15
Posts: 15
Reply #11 on : Mon December 12, 2011, 17:45:38
Mo
Posts: 15
Posts: 15
Reply #9 on : Mon November 28, 2011, 09:29:32
Mo
Posts: 15
Posts: 15
Reply #8 on : Mon November 28, 2011, 09:24:31
DPK
Posts: 15
Posts: 15
Reply #7 on : Fri November 18, 2011, 00:56:32
Amy Hsu
Posts: 15
Posts: 15
Reply #6 on : Thu September 29, 2011, 15:14:51
Anthony Garrett
Posts: 15
Posts: 15
Reply #5 on : Mon June 20, 2011, 12:46:52
Nicogis
Posts: 15
Posts: 15
Reply #4 on : Tue April 12, 2011, 11:01:02
Nelson
Posts: 15
Posts: 15
Reply #3 on : Thu April 07, 2011, 09:49:21
Eugene Honor
Posts: 15
Posts: 15
Reply #2 on : Fri April 01, 2011, 08:30:27
Clive Nicholson
Posts: 15
Posts: 15
Reply #1 on : Mon February 14, 2011, 06:10:57



No comments:
Post a Comment